Asset & Privacy OPSEC Starts Here
Your Data Is Vulnerable
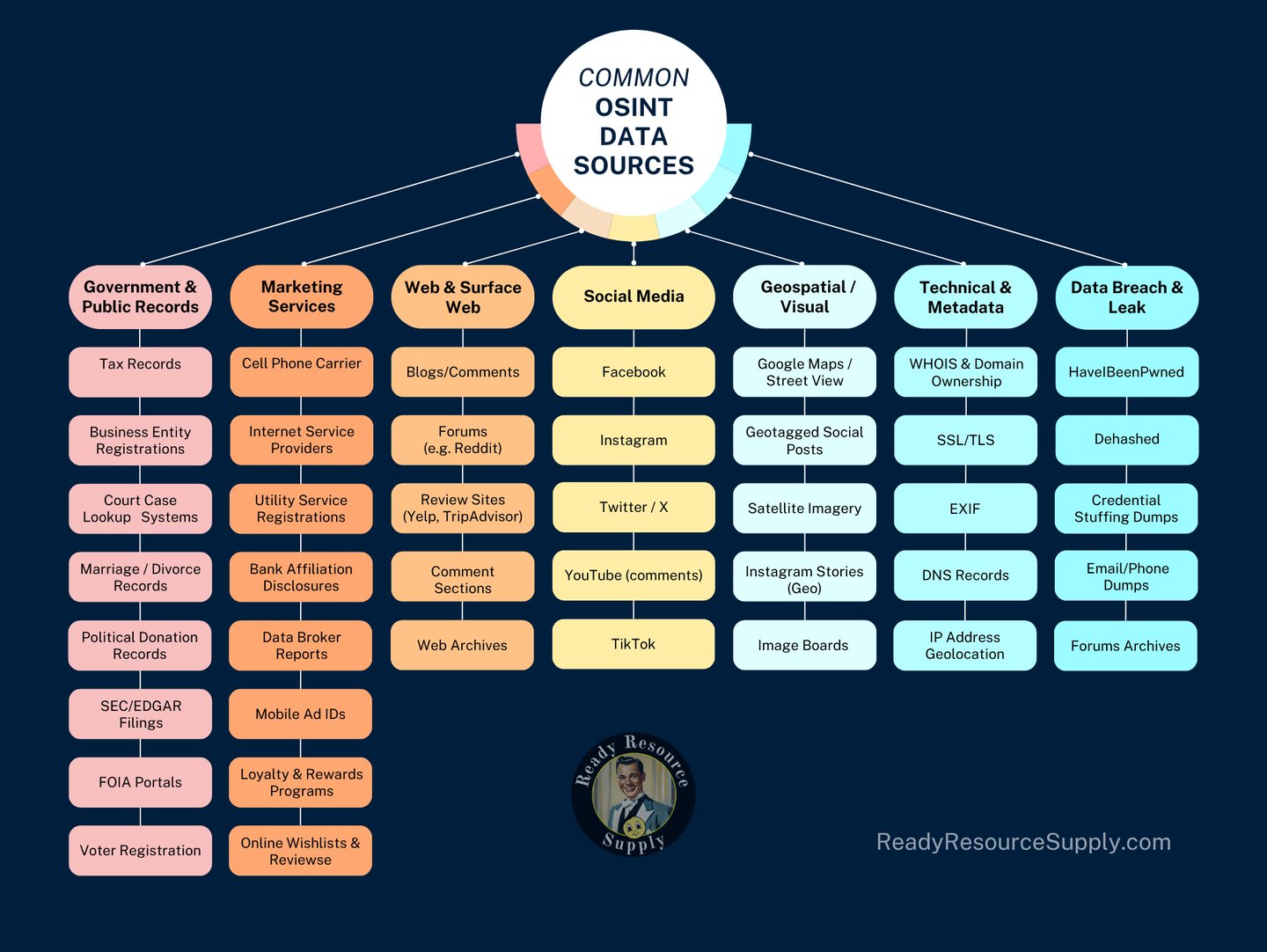
What OSINT (Open Source Intelligence) Looks Like
Below you will find an OSINT map of common exposure points and information categories that adversaries, data brokers, or even curious individuals can extract from public or leaked sources. This visual layout is designed to help you understand where your personal, financial, or asset-related data may be vulnerable—and how that information could be used against you. By identifying these areas, we can begin to take control of your public & digital footprint, tighten up your privacy, and implement proactive OPSEC strategies that fit your unique situation.
Counter-OSINT
OSINT—is different for everyone, because your digital footprint, public records, and exposure points are as unique as your fingerprint. What might be harmless for one person can be a vulnerability for another. I help clients harness OSINT not just as a threat, but as a powerful tool. By analyzing what information is publicly available about you or your assets, we can identify risks, close privacy gaps, and even turn the tables—using OSINT to monitor exposure, vet partners, or protect your brand. Whether you're a homeowner, investor, or entrepreneur, understanding your OSINT profile is the first step to taking control of your assets and privacy.
I work with anyone seeking greater control and protection, but I also specialize in supporting high-profile or high-risk individuals, retirees, law enforcement, veterans, military personnel, former military contractors, those with sensitive backgrounds, and more...
Discrete. Secure. Proven.
© 2025. All rights reserved.

For educational and informational purposes.
I am not an attorney, CPA, or financial advisor and this website is not intended to serve as legal advice. The contents of this website, social media, related information, or product collection are for informational and educational purposes only and may not be suitable for your specific situation or comply with the laws of your jurisdiction. I am not liable for any outcomes resulting from the use, misuse, or interpretation of this website, social media, related information, or product collection thereof. By visiting this page or purchasing any products, you acknowledge and agree to use this product or website information at your own discretion and risk. Use of any material on or associated with this website does not create an attorney-CPA-advisor to client relationship.